
MEET SUBSCRIBEManage all your private fund investments from start to finish on SUBSCRIBE
Centralize fund investments on a platform that offers the widest set of features available across pre-trade, trade, and post-trade investment workflows.
Request demo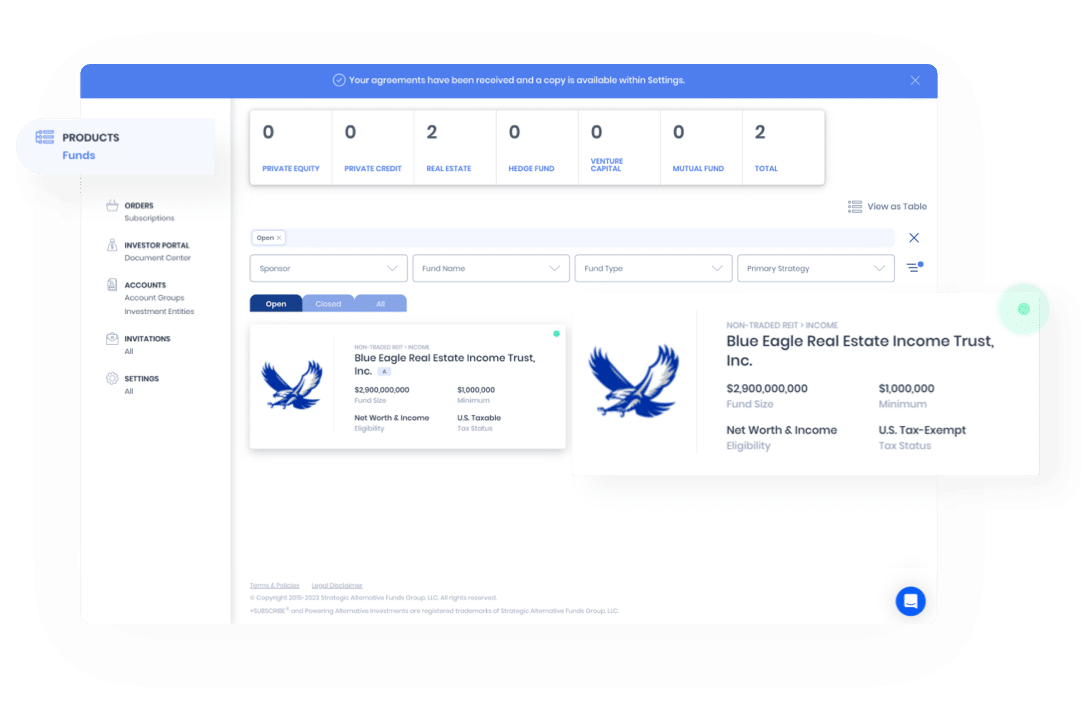
-
- Pre-Trade
Fund Raising Data Rooms
Secure data rooms with granular permissions, jurisdiction controls, & reporting combine with digital investor onboarding and subscriptions.
-
- Pre-Trade
Digital Investor Onboarding
Create reusable investor data passports for each investment entity that complete paperwork for any fund investment.
-
- Trade
Electronic Subscriptions
Upload subscription forms to digitalize them, then click a button to automagically prepare and sign the entire packet in seconds.
-
- Trade
Electronic Signatures
Collect signatures via a secure and compliant integration with Docusign. Globally accepted and enhanced with AES, QES, IDV, SMS, KBA.
-
- Pre-Trade
- Trade
- Post-Trade
Compliance Controls
Compliance supervision tools deliver controls throughout the investment workflow with custom product, investor, advisor, and order rules.
-
- Pre-Trade
- Trade
- Post-Trade
AML, KYC, FATCA, CRS
Managed services to collect, review, and monitor investor data & AML/KYC documents across funds and service providers.
-
- Pre-Trade
Account Pre-Qualification
Pre-qualify accounts for alternative products, manage compliance forms, and requirements in a streamlined interactive workflow.
-
- Pre-Trade
Product Saleskit Delivery
Meet regulatory requirements with an electronic saleskit module embedded in the transaction workflow (e.g. PPM, prospectus).
-
- Post-Trade
Investor Portal
Manage and track investments, updates, taxes, capital calls, distributions & financial statements all in one place - automatically.
-
- Post-Trade
Capital Call Management
Centralize capital calls to ensure timely completion, recording, accurate data capture, and syncing with your reporting software.
-
- Post-Trade
Distribution Management
Automatically capture and manage capital flows related to your investments and send data downstream to your reporting software.
-
- Post-Trade
Tax Automation Center
Automatically retrieve tax documents, extract critical data, track K-1 & K-3 reporting schedules, and collaborate with tax preparers.
-
- Post-Trade
PDF Document Collection
Automatically retrieve reporting documents from portals & emails – to organize, extract, validate, and send data to other systems.
-
- Post-Trade
PDF Data Extraction
Digitalize, organize, validate, and sync data with machine learning technology for document collection and data extraction.
-
- Post-Trade
Reporting Integrations
Leverage open-APIs to send fund and investment position level data downstream to your performance reporting software.
-
- Pre-Trade
- Trade
- Post-Trade
CRM Integrations
Leverage open-APIs to connect investor and fund transaction data upstream to your CRM for data syncing and order status monitoring.
-
- Pre-Trade
- Trade
Side Letter Management
Include side letters in the investment workflow, track clauses across funds & investors to simplify the MFN compendium.
-
- Trade
Blue Sky Tracking
Automatically identify submissions subject to blue sky exemptions, apply codes, and track data across different closings and funds.
-
- Trade
Supplemental Forms
Include, fill, and electronically sign any third-party firm documents required as part of the investment process.
-
- Pre-Trade
Education Center
Deliver investment strategy education and product test requirements ensuring advisor comprehension and regulatory compliance.
-
- Pre-Trade
Product Marketplace
Expand your alts access and streamline your alternative investing processes all at once with SUBSCRIBE Marketplace.
-
- Pre-Trade
Fund Select List
Access a menu of highly curated strategies along with independent third-party due diligence reports.
-
- Pre-Trade
Custom Fund Solutions
Form custom fund structures and low-cost feeders across single-manager and multi-manager funds in any jurisdiction.
-
- Pre-Trade
- Trade
- Post-Trade
Customer Support Team
Our dedicated customer support team ensures high levels of system adoption and superior customer experience.
-
- Pre-Trade
- Trade
- Post-Trade
White Label Sites
Implement an entirely customized white label site that integrates with internal systems, synchronizes data from CRMs, allows single-sign-on from current portals, and is themed for your organization.
-
- Trade
Issues Management
Digitally manage, monitor, and communicate service provider feedback on submissions with real-time order status tracking and in-platform issues and reconciliation modules that are logged and integrated with law firm and administrator listservs.
-
- Trade
Bulk Trades
Scale alternative fund investments across multiple accounts and multiple funds with a single workflow that consolidates the subscription process for investors in a single Docusign.
-
- Pre-Trade
- Trade
- Post-Trade
Model Portfolio Transactions
Allocate to alternative fund investments using model portfolios that can be custom configured for your organization and allow for a consolidated singular subscription workflow .
-
- Trade
SMA Transactions
Seamlessly prepare all separately manage account paperwork in a single platform using our master investor profiles that populate any investment management agreements and all custodian forms.
-
- Pre-Trade
- Trade
- Post-Trade
TAMP Integrations
Trading and rebalancing integrations are possible using our order APIs to help incorporate alternatives in to portfolios and manage exposures over the investment lifecycle.
-
- Trade
Custodian Integrations
Seamless integrations with the alternative investment workflows at Fidelity, Schwab, BNY Pershing and other custodians - including AI forms, Docusign, and delivery of paperwork and trade information to their systems.
-
- Trade
- Post-Trade
Secondaries
Digitally manage the paperwork for a secondary fund sale or purchase transaction in a secure and collaborative workflow that incorporates fund managers, fund investors, and service providers.
-
- Pre-Trade
- Trade
- Post-Trade
Role Based Access Controls
Manage access to sensitive data and functionality using our granular role and team based controls that are ideal for large complex organizations with multiple stakeholder groups.
-
- Pre-Trade
- Trade
- Post-Trade
Open-Architecture Invitations
Securely connect any fund manager, fund investor, or service provider counterparty to your fund investment workflows with a simple email invitation.
-
- Pre-Trade
- Trade
- Post-Trade
Investor Database
Gain a central view of prospective and current limited partners to manage order status tracking, investment reporting, and new fundraising campaigns.
-
- Pre-Trade
Custom Fund Menu
Centralize current and prospective fund investments along with their data and documents on the platform to create a custom fund database and menu for your organization.
-
- Pre-Trade
- Trade
- Post-Trade
Website Integrations
Implement a compliant web-based investment flow that is seamlessly embedded in to public fund marketing websites white labeled for your organization.
-
- Pre-Trade
- Trade
- Post-Trade
Custom Functionality
If you do not see functionality that your firm requires to digitally transform, connect with us, and we can create a custom development plan to solve for your specific needs.
ENTERPRISE INTEGRATIONS & SECURITYConfidently interoperate with enterprise grade security
SUBSCRIBE uses a combination of leading industry standards for security, tailored to keep client data safe from all angles. Our platform offers secure APIs allowing seamless data connectivity upstream and downstream with third-party softwares and platforms — CRMs, performance reporting softwares, asset custodians, accreditation services, payment platforms, or any proprietary endpoints.
Inquire about integrationsSOC2-Type-II Compliant
Ensuring strict adherence to trust service principles, we fully understand the importance of a mature and proven information security program in meeting our customers' goals.
Reliable Availability
We ensure the availability of our data and processing resources through regular reviews and testing of our disaster response plans. Our systems are deployed in geographically separated data centers.
Continuous Monitoring
We're always watching - rest assured, it's in a non-intrusive way. Whether through automated systems or personal interaction, we maintain constant oversight to ensure our systems are secure, reliable, and available.
In-Depth Defense and Layered Security
Multiple layers of security, including network and host-based firewalls, network and sub-network isolation, multi-factor authentication, and a low attack surface.
Global Data Compliance
We maintain the highest standard when handling data across jurisdictions. We are compliant with GDPR, CCPA, and Canadian data regulations, localizing data based on client needs in different geographic data centers.
Penetration Testing
We conduct penetration tests periodically to deliver a secure application. Our tests monitor the already low attack surface in the most realistic way possible, and then identify weaknesses that may lead to paths of compromise.
Vulnerability Scans
We run automated vulnerability scans and conduct proactive patch management. Additionally, we regularly perform data-driven risk assessments.
AES256 Encryption
Everything is encrypted both at rest and in transit. Confidential data is always encrypted on both the client and server sides.
Multi-Factor Authentication
Two-factor authentication adds an extra layer of security to ensure that you are the only person who can access your account, even if someone knows your password.
